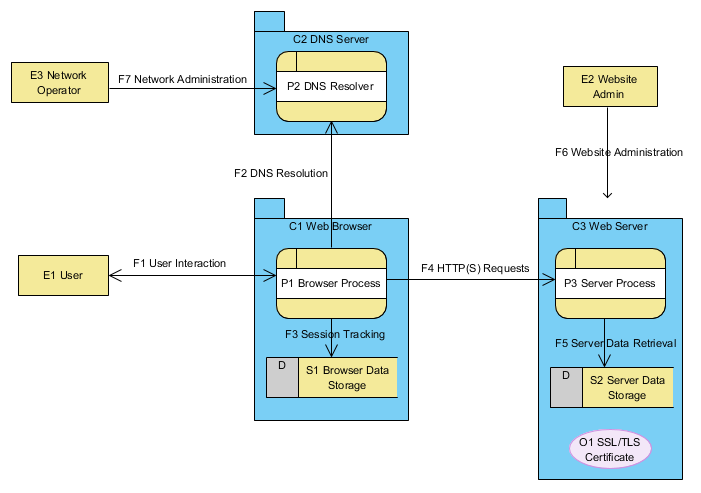
The @w3c Security #InterestGroup proposes to make systematic use of threat modeling in W3C to identify potential #threats, vulnerabilities, and safeguards in web specifications.
This guide is designed to help standards #developers make informed decisions about #security and #privacy risks from the beginning of standard development #timetogiveinput
▶️ https://www.w3.org/TR/threat-modeling-guide/
Feedback wlc: https://github.com/w3c/threat-modeling-guide/issues