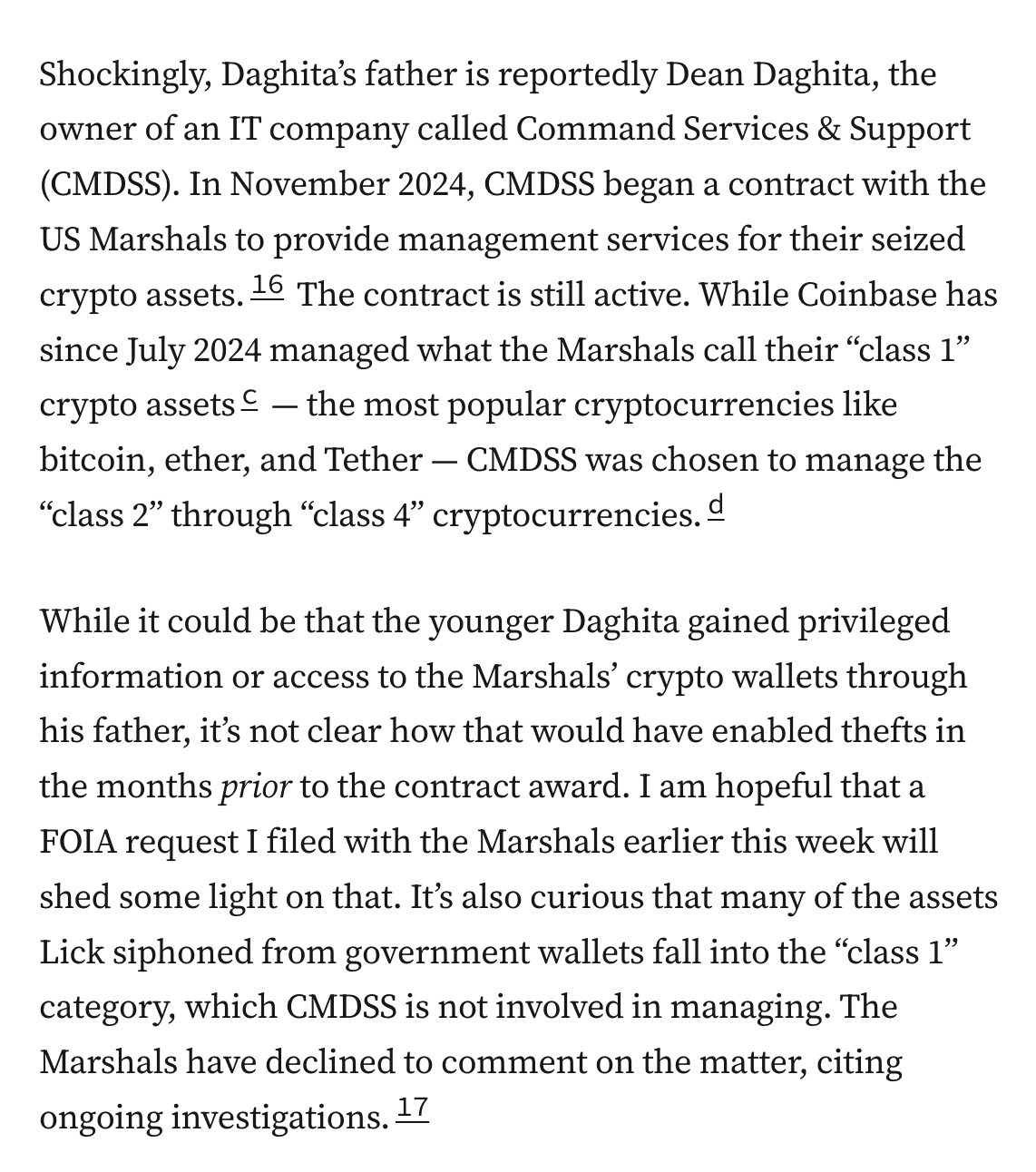
The incident has renewed concerns about the US government’s ability to prudently manage crypto. In 2022, a Department of Justice Inspector General report identified “challenges” in the Marshals’ crypto custody practices, including “lack of comprehensive inventory management” and “inadequate, incomplete, and conflicting policies and procedures”.18 Last year, the Marshals struggled to provide even an estimate of how much crypto they held. An IT contractor who was passed over for a contract with the Marshals explained to CoinDesk, “As far as I’m aware, the USMS is currently managing this with individual keystrokes in an Excel spreadsheet. ... They’re one bad day away from a billion-dollar mistake.”19 Later in 2024, the Marshals disclosed in response to a FOIA request that they held around 28,988 BTC (more than $2.5 billion at today’s prices), though they did not provide an accounting of their other tokens.20
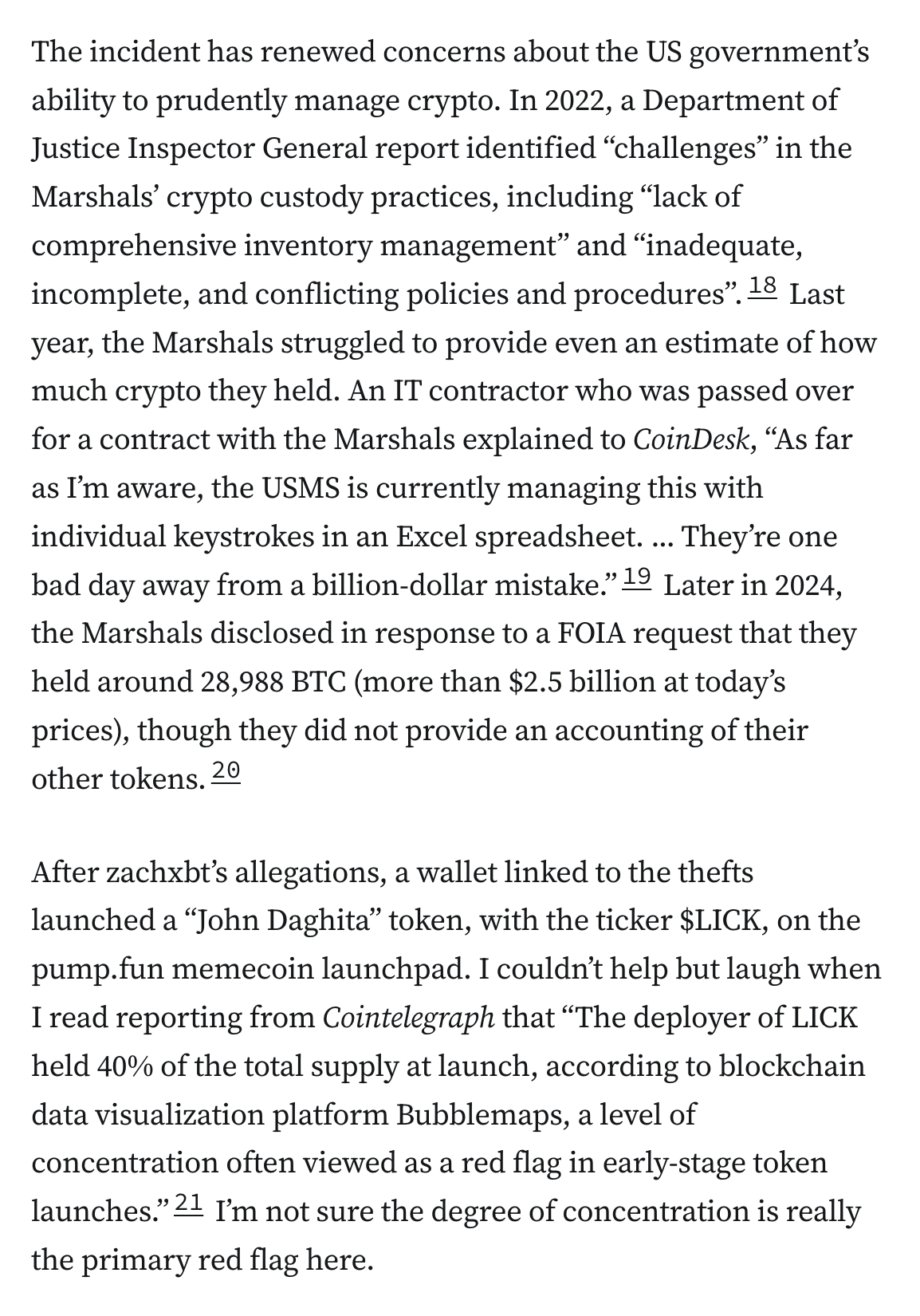
After zachxbt’s allegations, a wallet linked to the thefts launched a “John Daghita” token, with the ticker $LICK, on the pump.fun memecoin launchpad. I couldn’t help but laugh when I read reporting from Cointelegraph that “The deployer of LICK held 40% of the total supply at launch, according to blockchain data visualization platform Bubblemaps, a level of concentration often viewed as a red flag in early-stage token launches.”21 I’m not sure the degree of concentration is really the primary red flag here.
![In crime
Something funky’s been happening with the US Marshals’ pile of seized crypto — the crypto they’re tasked with hanging on to as cases wind through the courts.b In March 2024, almost $25 million was inexplicably removed from a Marshals-controlled wallet containing funds connected to the 2016 Bitfinex hack. In October 2024, crypto sleuth zachxbt noticed that $20 million of the Marshals’ crypto assets had apparently been stolen, with the thief laundering the funds through various exchanges [W3IGG]. The next day, $19.3 million of those funds were mysteriously returned.
Now, zachxbt has linked the stolen government funds — as well as stolen assets belonging to other victims — to a man named John Daghita. According to zachxbt, Daghita was previously known only as “Lick” online, and was active in Telegram chat rooms where crypto thieves boasted about their wealth. When another thief taunted Lick for “only having $6 mil”, Lick evidently decided the only way to defend his honor was to go on a screenshare call to show proof of ownership by transferring funds between wallets. In doing so, he exposed several wallet addresses, and zachxbt was able to trace some of the crypto back to the US government wallet addresses.1415](https://media.hachyderm.io/media_attachments/files/115/980/746/050/902/338/original/07d8150a201e98e2.png)